The Web-enabled Temporal Analysis System (WebTAS Enterprise, or just WebTAS) is both a collection of tools for intelligence analysts that can pull data from databases or websites and then chart, manipulate, and disseminate their conclusions as well as being a suite of tools and secruity frameworks for use by software developers to enable quicker development of applications designed for use in secure environments.
For the analysts, WebTAS provides Topic Builder (which has its own evaluation and is discussed only briefly here) and the Project Tool, which enables the integration of data from multiple sources and provides ways of visualizing and manipulating that data for analysis, display, and dissemination.
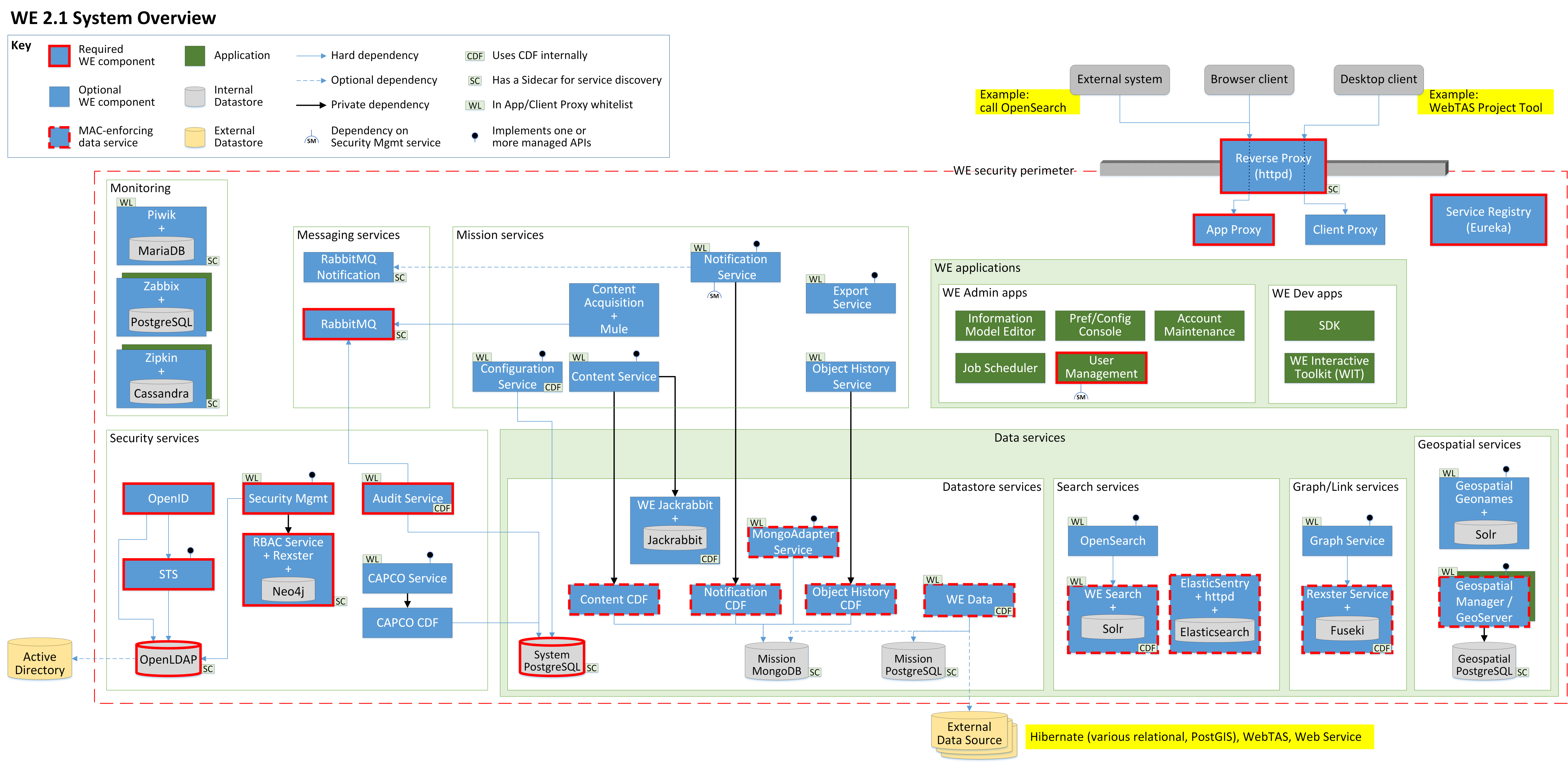
For the software developer, WebTAS provides a suite of open source tools inside an accredited security umbrella. Any particular deployment of WebTAS can use some or all of the available tools, enabling customization without having to write any specialized software. WebTAS also supports including custom applications both by enabling those custom applications to integrate with existing ones and by exposing interfaces to the installed tools. WebTAS makes extensive use of Docker. Consequently, WebTAS will integrate well in any software ecosystem that also uses Docker.
The following is a summary of each of the identified sections and the applications installed by default:
- Topic Builder. Enables the scanning and collecting of data from multiple text sources, such as news websites.
- GeoServer. A map server that, among other possible uses, enables Topic Builder to generate maps for displaying spatial data without the need for Google Maps.
- Information Model Editor ( IME). Sets up database connections between existing databases and WebTAS. Various SQL and NoSQL databases are supported. This enables WebTAS to pull data from multiple existing database systems.
- Web-based WebTAS Enterprise Project Tool. Enables users to employ most of the rest of the functionality built into the default install of WebTAS. Additional functionality would require the native version of the Project Tool or a custom application developed inside of WebTAS. Through the web app, users can create and manage database queries, create and manage map views and integrations (using GeoServer and or Google Earth), chart and display data in numerous ways, perform basic data management tasks, and create and administer electronic surveys.
- Security Services. Provides for user authentication, single sign on (SSO), user management, and auditing.
- Security Perimeter. These tools provide the interface between applications and tools in WebTAS and those using WebTAS. Applications deployed inside of WebTAS can be added as Docker containers to the servers that run the rest of WebTAS. Applications that use WebTAS can get security authentications and tokens from the WebTAS security services, but are generally deployed on different servers.
- Service Registry. Tracks and reports on all of the available services in WebTAS.
- Data Services (recommended tools). Provides a unified interface to a variety of external databases and data sources. This would enable an application to retrieve and manage data from multiple divisions without having to make redundant copies of the data. In other words, these tools extend the capability of the IME.
- Monitoring Services (optional tools). Can create an overall view of the system health, traffic, usage, etc. Dashboards and other similar services can be optionally configured, but are not available by default.
- Messaging Services (optional tools). This is, essentially, a RabbitMQ instance. This provides a quick and efficient path for different programs to communicate with each other without every service knowing about all of the other services.
- Mission Services (optional tools). Various content acquisition and export services.
How Do You Use It
WebTAS is installed onto a local cluster of at least 3 nodes with a fourth node serving as a host for the local file repository. A web portal is available for Internet Explorer and Firefox that exposes all of the tools inside of WebTAS.
Potential Use-Cases
WebTAS is government owned software and some organizations are encouraged to use such software.
WebTAS’s Topic Builder can, for example, parse the news reports from the past year from popular news outlets and create a report of everything related to North Korea, broken down by a variety of customizable criteria.
The Project Tool can be used to create a dashboard which combines results from database queries, derived graphs, maps, and google earth all in one display.
Scope of Evaluation
A full evaluation was performed for WebTAS. This included reading the provided documentation, researching the asset on Google, installation onto our own network, loading data from sources other than the asset provider, generating and performing various tests on the software, completing all of the checklist questions, and writing all of the summaries and explanatory content. As part of this evaluation we worked with the asset provider, especially in regard to installation.
Architecture Summary
WebTAS is architected as a distributed micro-service suite of tools which can support Single Page Applications (SPA) and Progressive Web Apps (PWA). In other words, the functionality of WebTAS has been split up into multiple Docker containers. Picking and choosing which Docker containers to deploy brings flexibility to a deployment, but dependencies between containers can make debugging more difficult.
Installation Summary
Installing WebTAS is very difficult without direct support from the developers. Very large (based on the typical system sizes at the time of writing) computer nodes are required for installation and the long term stability of the system was questionable at best during our testing.
Testing Summary
Only limited testing was possible on our install of WebTAS. Although all of the default tools were eventually installed, we were unable to ingest data from an external database (a core feature of WebTAS) which limited the scope of the tests that could be run. All of the other tools appeared to be functional.
Conclusion
For developers, WebTAS provides a good collection of commonly used tools inside an accredited security framework. Using WebTAS can allow for abstracting out many of the tedious details associated with creating such a framework from scratch, but WebTAS itself brings with it a difficult install and potential integration issues.
For analysts, WebTAS provides a lot of functionality, especially in the Topic Builder and Project Tool applications.
In summary, the key take-aways for this report are the following:
- WebTAS is both a set of ready to go tools for analysts and a set of open source building blocks for developers.
- WebTAS is of value to the DI2E community because it can provide an accredited security umbrella for development with common open source tools for developers and provides Topic Builder and the Project Tool for analysts, both of which can be incorporated into other, higher level, projects.
- The remainder of the report includes and addresses the following areas:
- Architecture Overview
- Installation details
- Test cases and details
- Checklist questions
- Checklist summary